By CTI | Mar 08, 2019 | Product of the Month
News stories detailing breach reports have become commonplace; it’s almost unusual to browse an online news site and not find a story about the latest mega-breach. Recently, DLA Piper published a startling finding that over 59,000 breaches have been reported across Europe alone since GDPR became effective in May 2018. Ninety-one (91) of those breaches resulted in fines. This new paradigm of daily breaches has IT and security management personnel worrying about their own safety measures, which leads to a few questions:
- Has my organization taken the time to identify all of the elements of a properly planned and effectively managed cybersecurity program?
- Have we acquired and deployed the necessary safeguards to protect organizational assets?
- Do we have sufficient training and staffing to quickly detect a cybersecurity event or attack?
- How well or how quickly could we take action to respond to a detected cybersecurity incident?
- Are we able to recover from a cybersecurity incident quickly enough to prevent long-term damage to the organization?
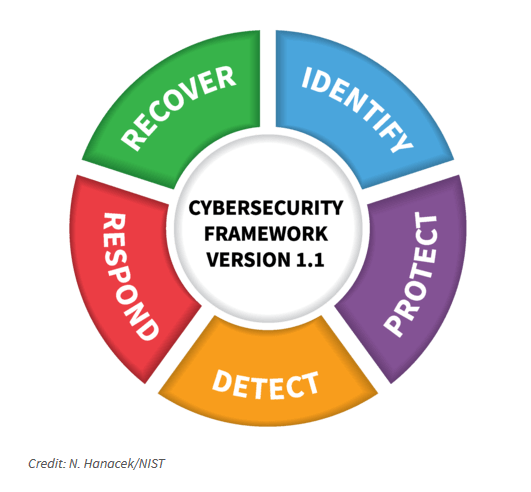
Wouldn’t it be great if a single information security standard could help an organization answer each one of these questions and evaluate its overall cybersecurity preparedness? Enter NIST’s Cybersecurity Framework (“CSF”)…
Originally released in February 2014 in response to Executive Order 13636, the second and most current iteration of the CSF (version 1.1) was released in April 2018. A broad spectrum of industries have either directly adopted CSF 1.1 or adapted elements of the Framework to support other pre-existing information security practices. An excellent example of CSF adaptation can be found in the U.S. Department of Health and Human Services’ (“HHS”) recent Health Industry Cybersecurity Practices publication, which openly leverages CSF terms and concepts.
CTI’s most comprehensive security controls assessment, SHIELDControls Pro, was designed around the CSF. By leveraging the CSF, CTI has ensured that this thorough evaluation will be directly applicable to the broad spectrum of industries that have either directly adopted the CSF, or have adapted elements of the CSF to a customized internal security program.
A SHIELDControls Pro assessment will enable you to easily:
- Perform a thorough review of the security and privacy controls currently deployed to protect organizational assets and identify any gaps (missing controls), as recommended by NIST SP 800-53r5 and the Center for Internet Security’s Top 20 Critical Security Controls.
- Evaluate your organization’s security and privacy management practices with reference to the five (5) major security functions described by the NIST Cybersecurity Framework – Identify, Protect, Detect, Respond, and Recover.
- Understand the organization’s level of compliance with a variety of well-known information security frameworks and regulations, such as HIPAA, HHS HICP, HITRUST, FFIEC, PCI DSS, and DFARS.
- Establish metrics—such as NIST 800-53 control baselines and CSF profiles—to track year-over-year improvements in security capabilities.
- Communicate assessment findings to executive management in preparation for budget cycles and security program planning.
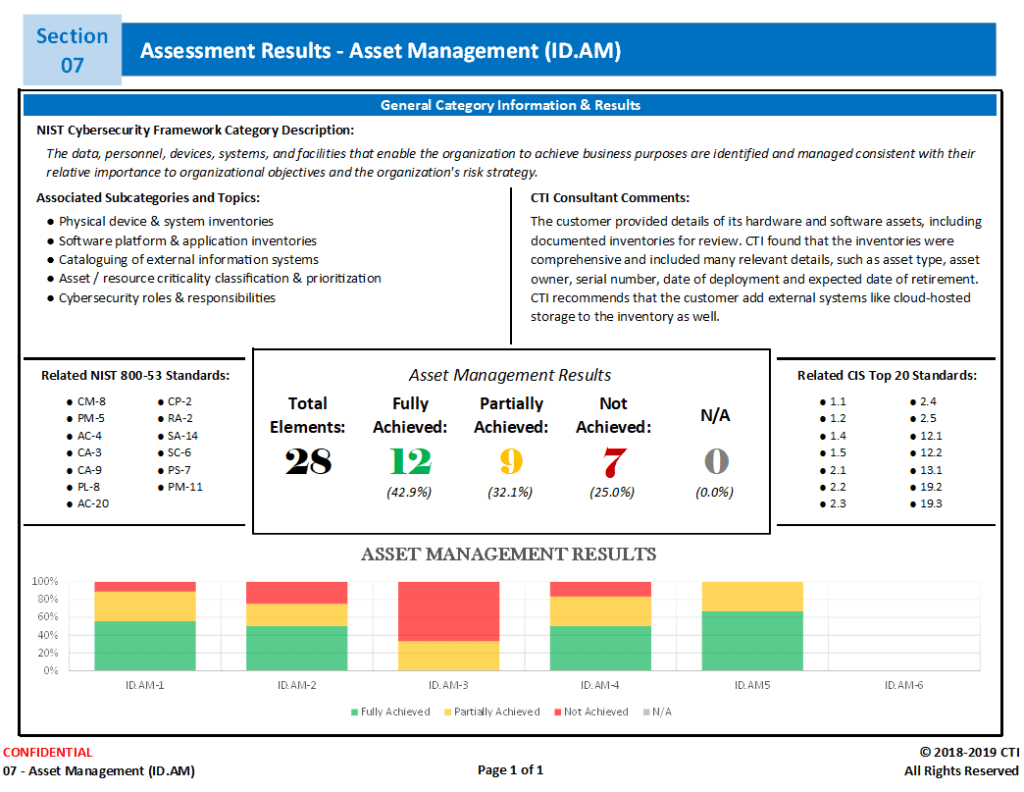
Once the SHIELDControls Pro Assessment is complete, you will receive a comprehensive report that includes the Asset Management results and personalized suggestions from CTI consultants, all laid out in a clear and concise report.
Don’t spend your days wondering whether you’ve really prepared your organization to address a cybersecurity incident—give CTI a call! Take the first step towards a confident understanding of your organization’s security posture and its ability to identify, protect, detect, respond, and recover from cybersecurity incidents.

